Protecting Java Software Applications - Arxan Best Practices White Paper
←
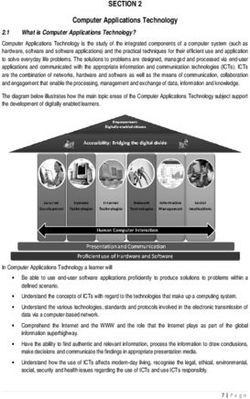
→
Page content transcription
If your browser does not render page correctly, please read the page content below
Protecting Java Software Applications Arxan Best Practices White Paper Arxan Technologies White Paper – Arxan protects your IP from software piracy, tampering, reverse engineering and any manner of theft. 1
TABLE OF CONTENTS
Executive Summary 3
Java Is Powerful, But Also Vulnerable 4
ons
Attacking and Defending Java Applications 7
Deploying GuardIT® for Java
ava 8
Arxan Technologies White Paper – Arxan protects your IP from software piracy, tampering, reverse engineering and any manner of theft. 2Executive Summary
Java is widely used in web application programming. Web and enterprise applications are predominantly
programmed in Java today. Java is widely used to build IP-intensive thick client applications such as banking
clients, social networking clients and MMORPG game clients; and in software powered devices such as routers,
embedded controllers, firewall devices and digital media devices. Ease of development, cross-platform support
and increasing performance are all factors driving Java adoption.
Java code is easily hacked, making IP and sensitive data vulnerable. Java code, being a managed
language distributed as intermediate-level byte code, is highly susceptible to reverse engineering and
tampering attacks. This allows IP theft, data theft and piracy. Ease of code analysis also enables rapid
vulnerability discovery, which in turn accelerates the development of damaging malware. As malware moves up
the stack to the application layer, insider attacks continue to rise, and IP is targeted by hackers, securing Java
code against compromise is vital to safeguarding of an organization’s software and data assets.
Java protection that really works. Enterprises and software vendors are generally aware of the need
to protect Java software – whether thick clients, thin clients or enterprise applications. To date, however,
the main technology available for protection comprises superficial techniques such as string encryption and
variable renaming. Such methods are easily reversed and have a short effective shelf life, leading to the myth
that Java cannot be protected. In reality, string encryption and variable renaming form a useful first layer, but
are quite inadequate when used in isolation. Arxan combines these popular measures with strong binary-level
obfuscation and secure class loading for meaningful protection. Additionally, we provide tamper-evidence to
achieve longevity of protection, providing real time security alerts of potential system compromise and allowing
software and its managers to react intelligently – for example by self-healing exploits or proactively initiating a
security layer renewal.
GuardIT® secures your software ecosystem. Arxan’s GuardIT for Java provides a multi-pronged
solution to durably fortify your Java code against disassembly, static analysis, dynamic analysis and tampering. The
diagram below shows how GuardIT for Java secures code, keys and data throughout the client and server layers
of the enterprise. GuardIT for Java also provides defense in depth for perimeter security measures, and enables
secure communication (e.g. for tamper evidence notification or forensics information) across components.
Arxan Technologies White Paper – Arxan protects your IP from software piracy, tampering, reverse engineering and any manner of theft. 3GuardIT for Java is part of the GuardIT family of products, which protects desktop, server and embedded
software against malware, IP theft, piracy and tampering on a variety of platforms. GuardIT is the only solution
on the market today which seamlessly enables protection spanning managed and native portions of your C/
C++, Java, mixed-mode and Java applications.
Java Is Powerful, But Also Vulnerable
Web applications and enterprise applications for data management, financial transactions, e-commerce and
internal productivity are predominantly coded in Java today. Java is also increasingly used in developing thick
client applications that have traditionally been coded as native desktop applications. The major problem with
Java, however, is that it is very easily reverse engineered.
Java byte code is intermediate code, rich in metadata and semantic information. It is trivially easy to reverse
the Java assembly process. There are a number of free or low cost decompilers such as JAD and DJ which can
analyze Java binaries and reconstruct the original source to near perfection. Trends such as outsourcing of
development and testing to third party vendors, and the increasing incidence of insider attacks on information
security systems, magnify the risk to enterprise applications. This gives rise to the following consequences:
• It is trivial for hackers to steal IP, construct tampering exploits to disable security functions,
or discover vulnerabilities and build malware exploits.
• Interfaces between the application and security measures such as license management or
user authentication are particularly vulnerable.
• Hard coded credentials, secrets in Java key stores, and similar sensitive assets are easily
discovered and abused.
• Feature-rich web 2.0 client applications require special attention to protect them against
hackers and malware.
Once hackers find vulnerabilities in the application, they construct exploits to leverage these in the wild.
Examples of exploits include:
• In the case of enterprise and web applications, the majority of exploits is built to enable theft
of sensitive data – whether from backend databases or from client front ends.
• In the case of licensed software, exploits are built to enable piracy – by circumventing license
management, or by building counterfeits. These tampering attacks are particularly easy on
unprotected Java applications. The hacker simply decompiles the binary into source, makes
the necessary edits, and recompiles.
• In cases of both enterprise and desktop applications, exploits to inject malware - whether by
exploiting input-based vulnerabilities or by compromising the authentication methods designed to
securely update deployed software.
The Client Tier
Client tier applications, thick client applets and thin clients run in hostile, untrusted environments. They per-
form real work in terms of validation, data processing and calculations. In the case of desktop applications,
they also incorporate significant proprietary IP and generally have a license management component. Code
in the client tier generally exposes business logic, hard coded credentials, SQL query structure, and similar
sensitive information. These assets are easy targets of attack since hackers have complete control over the
client and its execution environment.
Clients are vulnerable to reverse engineering to discover these assets, and exploitable vulnerabilities in both
the client and the backend enterprise system. They are also vulnerable to tampering attacks for data and IP
theft, as well as malicious invasions of the backend server. Attackers simply decompile the client code, which
they have full access to. They then edit the code as necessary, and recompile.
Arxan Technologies White Paper – Arxan protects your IP from software piracy, tampering, reverse engineering and any manner of theft. 4The Web Tier Web tier applications include those running in a data management zone (DMZ) as well as those running inter- nally in the enterprise. Such applications are somewhat protected by perimeter security measures such as intru- sion detection systems and web application firewalls (WAFs). However, they are still vulnerable to exploitation by malware and to insider attacks. Studies show, for example, that over 60% of departing employees steal corporate data. Employees and system administrators often have access to hard coded credentials and keys that can also be abused. Additionally, employees can unwittingly infect their computers with malware, subsequently exposing internal data and applications to compromise. As companies expand to selling in emerging markets and outsourcing service units to other countries, web tier applications are increasingly vulnerable to reverse engineering and tampering attacks. Web tier applications are vulnerable to reverse engineering to discover corporate IP, secure authentication credentials and keys embedded in the code. They require protection against malware injection and tampering. Real time security alerts regarding running applications, with information on tamper evidence and attempted intrusions, is particularly important for this class of applications. The Web Tier The diagram above and table below discuss the various types of assets at risk in the Java ecosystem, the types of threats used to exploit these assets. Arxan Technologies White Paper – Arxan protects your IP from software piracy, tampering, reverse engineering and any manner of theft. 5
Java Application Type Threats Resulting Compromise
Thick client or applet Reverse engineering • Discovery of proprietary IP such as
business logic
• Discovery of hard coded credentials
• Discovery of coding vulnerabilities exploitable
by insiders or malware
Tampering • Malware invasion
• Disabling authentication-based data access
control and similar data security functionality
• Altering functionality of gaming (MMORPG)
clients for cheating
Java Web Start Applications Tampering • Injection of malicious code
• Altering of security routines
Desktop applications Reverse engineering • Identification of proprietary IP
• Find vulnerabilities in license management
component, and in interface between
application and license management
• Find vulnerabilities in methods used to
authenticate software updates
Code lifting • Counterfeiting
Tampering • Widespread piracy of software
• Injection of malware into software platform
Thick or thin clients Reverse engineering • Discovery of secret keys used to prove identity
and secure internet communications
Perimeter security appliances- Tampering • Invasion by malware
such as a WAF or anti-malware
device
Web tier applications such Reverse engineering • Discovery of vulnerabilities exploitable
as servlets by malware
• Discovery of proprietary IP such as
business logic
• Discovery of hard coded credentials and
secret keys, and consequent data theft
Tampering • Malware invasion
Business tier applications such Reverse engineering • Discovery of vulnerabilities exploitable
as EJB model by malware
• Discovery of proprietary IP such as
business logic
• Discovery of hard coded credentials and
secret keys, and consequent data theft
Backendenterpriseapplications Reverse engineering • Discovery of vulnerabilities exploitable
and services by malware
• Discovery of proprietary IP such as
business logic
• Discovery of hard coded credentials and
secret keys, and consequent data theft
Tampering • Malware invasion
• Unauthorized access to data
• Unauthorized access to application or service
• Unauthorized use of application or service
Code lifting • Theft of proprietary business logic and
applications
Backend database Reverse engineering • Theft of proprietary business logic and
applications
Arxan Technologies White Paper – Arxan protects your IP from software piracy, tampering, reverse engineering and any manner of theft. 6Across all software segments and uses, hardening of Java applications is imperative to protect your intellectual
property and sensitive data against piracy, theft and malware. It is no surprise that application security is a
new top initiative among Fortune 1000 organizations.
Attacking and Defending Java Applications
Across all software segments and uses, hardening of Java applications is imperative to protect your intellectual
property and sensitive data against piracy, theft and malware. It is no surprise that application security is a
new top initiative among Fortune 1000 organizations.
STEP 1: Decompile the binary. This results in recovery of source code. Recovering high quality source
code is critical to the subsequent hacking process.
STEP 2: Comprehend the code. Based on the results of decompilation (step 1), the attacker analyzes and
attempts to comprehend the source code to identify valuable intellectual property, discover exploitable
vulnerabilities, and find secret keys. Popular targets include routines for license management, data access
management, transaction session management, and application extension/update channels.
STEP 3: Build the exploit. Knowledge acquired from comprehension (step 2) is used to build a tampering
or malware injection exploit.
Successful construction of an exploit is dependent on accurate comprehension of code, which in turn can
be achieved only after a high-quality decompilation. Traditional techniques to protect Java applications focus
on preventing comprehension of the reconstructed source code through string encryption and variable
renaming. GuardIT for Java provides effective and durable protection by hardening against all three phases of
the attack process. Salient protection features include:
• Control flow obfuscation. By breaking the correlation between byte code and semantically
meaningful source code constructs, the quality of decompilation is degraded. By removing structure
from the code, it eliminates tell tale patterns and breaks the predictable relationship between byte
code and decompiled source. This degrades the results of decompilation and makes comprehension
and reverse engineering very difficult. Rather than rely on tactics that break leading disassemblers, Arxan’s
obfuscation uses underlying language characteristics to achieve resistance to accurate decompilation. The
result is reliable, long-lived protection that is not hostage to an arms race between a protection solution
and decompiler enhancements. Strong control flow obfuscation is a crucial component of any effective
protection solution for Java.
• String encryption and variable renaming. By removing semantically meaningful variable names, strings
and thus context from the code, these commonly used techniques make the comprehension and reverse
engineering process more difficult and time consuming. While inadequate in isolation, they are a valuable
complement to strong obfuscation and encryption measures.
• Class File Encryption. By encrypting JAR files, and using custom class loaders at load time for
decryption, this blocks static reverse engineering and tampering of class files. This measure also
prevents injection of malicious code or methods into the class at run time, and provides robustness to
Java’s security hooks such as sealed classes and signature verification. Secure class file loading does
not alter the portability of Java byte code.
• Key Protection. Complementary to GuardIT for Java’s code and data protection capability is Arxan’s
TransformIT® white box cryptography technology. TransformIT provides strong protection for keys
used within Java applications – e.g. to encrypt sensitive data in databases, to encrypt communication
during a secure internet session or to verify credentials - against discovery and tampering.
• Real time security alerts. Arxan’s active protection technology provides real time security alerts with
full context from a running application. This tamper-evidence mechanism reports forensics information
back to an appropriate central entity (enterprise security management console) when malware invasion
or other forms of tampering are detected. This allows potential breaches to be dealt with quickly and
accurately, providing visibility and limiting damage. Since these application alerts have full knowledge of the
context of the application and its current state, security alerts are accurate and informative. The application
centric nature and secure communication capabilities of real time security alerts can be used by itself or
to work with and augment other security technologies such as SIEM, whitelisting and WAFs by providing
stronger application context.
Arxan Technologies White Paper – Arxan protects your IP from software piracy, tampering, reverse engineering and any manner of theft. 7Deploying GuardIT for Java
Fast. GuardIT for Java is applied directly to your compiled binary.
Easy. GuardIT for Java provides a host of easy-use features including wild-card inclusion and exclusion for
variable names and function names. This allows you to quickly and easily define which areas of your program
need protection. Protected binaries remain managed mode applications – there is no native compilation, and
you retain all the portability advantages of the Java platform.
Strong. GuardIT for Java is built to work closely with GuardIT®, Arxan’s flagship application hardening
solution for native applications. This makes GuardIT the only solution on the market today which seamlessly
enables protection spanning a variety of native and managed application development technologies across a
variety of operating systems and execution platforms.
For more information about GuardIT, GuardIT for Java, and maximizing your profits by minimizing your
application risk, please contact us at info@arxan.com or visit our website at www.arxan.com.
All Content and Arxan Trademarks (including logos and service marks) are protected by Copyright and Patents and
are the property of Arxan Technologies. ALL RIGHTS RESERVED, as specified at www.arxan.com/legal/index.
Arxan Technologies White Paper – Arxan protects your IP from software piracy, tampering, reverse engineering and any manner of theft. 8
1You can also read