Next Generation Deception Technology Vs. Honeypot Architecture - Illusive Networks
←
→
Page content transcription
If your browser does not render page correctly, please read the page content below
Deception Technology 101: A Quick Introduction
The idea of deceiving cyber attackers into thinking With deceptions placed everywhere throughout the
they’ve accessed valuable data isn’t a new network and on every attack surface, cyber security
innovation. In 1999, the Honeynet Project, a non- solutions grow stronger. Essentially, an entire maze
profit dedicated to improving Internet security, of inescapable deceptions can be placed over the
developed the first network of honeypot technology. network quickly, cost-effectively, and in a way that
is scalable for the future.
These decoy computer systems were designed to
purposely engage and deceive hackers in order to Both honeynets and next-gen deception technology
better understand their tactics and activities. The have their merits; understanding the key differences
idea was innovative and effective at the time, but between the two is critical for determining which
as environments became more sophisticated, solution can best help an organization defeat the
deception technology needed to follow suit. cyber criminals that step into its particular
environment.
Cyber security professionals with limited time and
resources reported that honeypot solutions were
limited in their extensibility, expensive and difficult Despite the increasing effort that
organizations are putting into keeping
to manage. Next-generation deception technology
intruders out of their networks, once
from Illusive Networks was created to overcome sophisticated attackers zero in on a specific
limitations inherent in honeypots. company or information source, there’s a
good chance they’ll find a way in.
Perimeter Defenses Aren’t Slowing Down Attackers
Cyber criminals grow more sophisticated each day, Reacting to the attacks is the exact problem.
and network security architectures aren’t evolving Honeynets and next-gen deceptions are markedly
quickly enough to keep up. different from traditional cyber security appliances
and architectural solutions. Where complicated
Despite increasing security investments and best
applications aim to react to a cyber attack and
efforts, industry studies and research continues to
isolate it as soon as possible, honeypot architectures
find that sophisticated malware authors and cyber
and next-gen deceptions take a more proactive
criminals are innovating at a faster pace than
stance to catch cyber criminals in the act.
security professionals can react to.
Attackers are increasingly able to slip past network
security applications such as IDSs, IPSs, firewalls,
and web application firewalls---regardless of how
new and comprehensive they are.Think Like an Attacker to
Create a Stronger Layer of
Security
The most notable difference between honeypot
architectures and a next-gen deceptions approach is
their ability to mimic real-world scenarios. Cyber
criminals have come to recognize there’s something Honeypots are incapable of
not quite right about honeypots, because they don’t
interacting with a spear phishing
behave like a real user-controlled environment.
When honeypots are deployed, they are configured attack the way end users do---
to behave in a certain way, and automated to carry meaning they won’t be able to track
out specific tasks to appear authentic to cyber
criminals. While this may have proven effective in
the criminal or the attack.
the past, attackers are no longer deceived as they
once were. Cyber Criminals are
For example, social engineering and spear phishing
Accustomed to Sniffing Out
attacks are an example of how honeypots can be
Honeypots
outsmarted. Many attacks today start out with a lure Understanding adversaries is essential for
that prompts a user to act in a way that allows constructing the defenses that will trap them. Here
malware in to infect the network. are some of the ways cyber criminals determine
whether or not a honeypot is in play:
Honeypots can scan for attachments, an old school
attack vector, but are incapable of interacting with
If access seems too easy, it’s probably a
a spear phishing attack the way end users do, fake.
meaning honeypots won’t be able to track the
Typically, systems connected to the
criminal or the attack. In contrast, next-gen
Internet are devoid of unnecessary ports
deception technology is far more adaptive. In fact, and services. Any deviation from this
it’s capable of changing deceptions automatically configuration could be indicative of a
trap.
and not remaining static---like an actual, dynamic
network with natural changes in user and network If the systems still have factory default
settings, this increases the chances of a
information. honeypot being present.
Honeypots are a much more static technology, If there’s a considerable amount of empty
covering only as much of the network as you can hard drive space or very little software
installed, it could be a honeypot.
physically integrate with multiple deployments.
Next-gen deception technology significantly covers If directories are obviously named (credit
card numbers, employee data), the
more attack vectors, identifying attackers within
systems are clearly aimed at luring in
three to four lateral movements—even if deceptions attackers.
aren't deployed on every machine.(cont’d) All of these warning signs tell cyber criminals that the system may not be legitimate.
In contrast, next-gen deception technology presents the attacker with endless elements of false information
that appear genuine, subtly deluding them to the point where the attacker is caught between knowing what is
real and what is illusion. This constitutes a more disorienting approach capable of misleading even the most
experienced cyber attacker.
Next-gen deceptions provide powerful attacker detection and real-time forensics, with virtually no false
positive alerts, and the attacker never knows his movements are being monitored. Honeypots provide value for
attacker detainment, but at the cost of more false positive alerts.
Red Teams Agree: Honeypots Fail in Comparison to
Inescapable, Next-Gen Deception Technology
In recent side-by-side Red Team Tests, honeypots provided “comparatively low detection rates with higher
maintenance and management costs. These solutions are context-less, one-dimensional, and difficult to scale
in a dynamic environment.” The ROI isn’t compelling for honeynet architectures.
On the other hand, next-gen deception technology was designed for the modern threat landscape. In Red
Team Tests, it received high marks across the board:
• Red Teams found the next-gen deception technology
extremely difficult to bypass. They set off thousands
of alerts as they tried to move laterally through the
EARLY DETECTION OF system. The attack was easily tracked and they were
LATERAL MOVEMENT. prevented from reaching their ultimate goal.
• Cyber criminals compromise systems by moving
AN APPROACH laterally between machines. Security deceptions
ATTACKERS CAN’T detect this early in the process, keeping track of real
time forensic data and complete attacker profiling.
SEE COMING.
• With a Vector-as-a-Resource (V2R) focus, next-gen
deceptions catch attackers off guard by appearing in
places that don’t coincide with old school methods.
V2R can be anywhere and everywhere on a network,
making it nearly impossible for attackers to detect
false scenarios.Inescapable Deceptions Vs.
Honeypots: Same Goal,
Different Appearance A Changing of the Guard
Both honeypots and next-gen deception technology Honeypot architecture was innovative at its
set out to proactively deceive and track cyber inception. It paved the way for a more proactive
criminals during the attack phase. That’s where the approach to cyber security and kept attackers at
similarities end. Each approach looks very different, bay.
from both the enterprise and criminal perspectives.
Yet, today, cyber criminals are more specialized,
Honeypots are hardware-based, physical systems targeted and innovative when it comes to seeking
that are deployed in the workplace and configured new attack vectors and circumventing both
like any other workstation. These static systems act perimeter defenses and old school honeypot traps.
as a sort of sandbox, luring attackers in with the In a few short years, the market for cyber security
promise of sensitive data and then keeping track of solutions will reach $200+ billion. Clearly,
their every move. companies can no longer afford to concentrate all of
their resources on firewalls and first line of defense
On the other hand, next-gen deceptions present a
systems.
“hall of mirrors.” False information is placed in the
path of attackers who will use the information in They also need to incorporate “internally focused”
their lateral movement infiltration phase. Attackers solutions such as next-gen deceptions to help
are methodical—they collect data, analyze it and identify a criminal while in attack mode. This type
calculate their next move as they relentlessly push of preemptive technology represents a changing of
through a network. the guard from old school strategies to more
outside-of-the-box thinking that can finally trace
and stop professional cyber criminals.
Cyber criminals are taking the time to analyze the
human psyche as they craft carefully designed
CROWN
JEWELS
malware lures. It’s time for cyber security
professionals to take a page out of the attackers’
Illusive’s next-gen deceptions takes advantage of play book and use a more realistic set of illusions to
this mindset and covers the entire network in a trap, track and thwart their actions from the start.
blanket of finely tuned lures designed to attract
For those that are serious about detecting attackers
cyber criminals, alert network administrators and
post-breach, Illusive’s inescapable, next-generation
disrupt the attack.
deception technology is a vital step.
Not only can companies proactively thwart attacks,
Where honeypots are confined, next-gen
they can also gather critical information that can deception technology is far more alluring
prove useful for future defense. and pervasive.The Illusive Platform
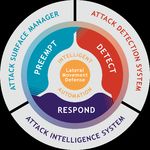
The Illusive Platform provides centralized management across even the largest and most distributed
environments. Three modular components work together or be operated separately to preempt, detect, and
respond to cyberattacks.
Preempt: Finds and removes errant credentials,
connections, and attack pathways to deter unauthorized
lateral movement.
Detect: Forces attackers to reveal themselves early in the
attack process by disorienting and manipulating their
decision-making.
Respond: Enables rapid, effective response and remediation
when attackers are present by providing contextual source
and target forensics.
Visit us at www.illusivenetworks.com
Email us at info@illusivenetworks.com
Call us at +1 844.455.8748 (North America) or +972 73.272.4006 (EMEA and AsiaPac)
Illusive Networks stops cyberattacks by destroying attackers’ ability to make
safe decisions as they attempt to move toward their targets. Using Illusive, ©2019 Illusive Networks Ltd.
organizations eliminate high-risk pathways to critical systems, detect
attackers early in the attack process, and capture real-time forensics that
focus and accelerate incident response and improve resilience. Through
simple, agentless technology, Illusive provides nimble, easy-to-use solutions
that enable organizations to continuously improve their cyber risk posture and
function with greater confidence and agility.You can also read