Multiple ASpects TrajEctoRy management and analysis - MASTER
←
→
Page content transcription
If your browser does not render page correctly, please read the page content below
Issue 1 | September 2018
Multiple ASpects TrajEctoRy
management and analysis
Inside this issue
3
Editorial
4 The MASTER project
7 Holistic trajectories, privacy, and
the strategic concealment/disclo-
sure of information
This project has received funding from the European Union’s Horizon 2020 research and innovation programme under the Marie Sklodowska-Curie
grant No 777695 Duration: March 1 2018 | February 28 2022 © 2018 MASTER www.master-project-h2020.eu3
Editorial
Welcome to the first issue of the MASTER newsletter. The objective of this newsletter is to keep the consortium updated with the
main activities that are going on during the project, summarizing the main interesting results in terms of secondments, training,
scientific results, vision and dissemination activities. We also want to communicate our main outcomes to a wider audience, find
more opportunities for collaborations and exchange of ideas with interested readers outside the consortium.
Our newsletter will be published every 6 months. Each issue will be available for download from the MASTER web site at
http://www.master-project-h2020.eu
In this first issue we introduce the project, the consortium and report about our kick off event held the last March 2018.
We are very happy and proud that our Independent Ethical Advisor Prof. Bettina Berendt accepted our invitation to prepare a
very stimulating article expressing her vision about the need of ethical consideration in data science for holistic trajectories. Prof.
Berendt shares her thoughts on two case studies: the well known New York taxi dataset and the controversial topic of the analysis
of ships traces for the detection of search and rescue operations in the Mediterranean Sea, linked to the migration phenomena.
Her vision will be our starting point for reflecting on the ethical issues that our research is posing.
The next issue will be published at the end of February 2019: we will report results from our secondments, selecting highlights on
the major research results and the plan for activities like the first MASTER Workshop and the planned Summer School.
Stay tuned and happy reading!
Chiara Renso, Project Coordinator4
MASTER NEWSLETTER - www.master-project-h2020.eu
The MASTER project
MASTER is a Horizon 2020 project under the programme Marie Sklodowska-Curie Actions - Re-
search and Innovation Staff Exchange (RISE) for boosting the carrier perspectives of researchers
through staff exchange
Chiara Renso, Project Coordinator, HPC Lab, ISTI-CNR, Italy
In our everyday life we interact with a senting the multiple aspects of move- We investigate methods for managing
number of diverse, real-life applications ment data. and building semantically rich trajecto-
that produce massive amounts of spa- ries from heterogeneous and multidi-
tio-temporal data representing trajec- In the MASTER (Multiple Aspects Trajec- mensional data.
tories of moving objects. For example, tory Management and Analysis) project How can we infer interesting knowl-
we can considering mobile phone calls, we call them holistic trajectories, mean- edge from large amounts of holistic tra-
GPS enabled tracking applications, (geo- ing trajectories characterized by the fact jectories?
tagged) social media but also land, sea, that space, time and semantics are all We study data analysis methods capa-
and air surveillance systems with smart different aspects that are intimately cor- ble of taking into account the different
APPLICATIONS
Tourism Sea monitoring Transportation
METHODS
Definition, construction
and management of holis- Analysis of holistic tra-
tic trajiectories jectories
Big Data Privacy Big Data Privacy
The concept of the MASTER research programme
sensors and public transportation like related and should be considered as a aspects of holistic trajectories. We focus
buses and metro. In all these areas, po- whole. Current state-of-the-art methods specifically on: similarity analysis, clus-
sitioning data is produced, collected, do not provide methods “ready for use” tering, graph analysis, prediction and
stored and analysed together with ad- for these multiple aspects trajectories. recommendation.
ditional contextual data. These trajecto- Which applications benefit from the
ry data is therefore evolving from pure THE MASTER PROJECT IN 5 analysis of holistic trajectories?
sequences of timestamps and position QUESTIONS: We assess the impact of the holistic tra-
coordinates to more comprehensive and How can we create and manage holistic jectories analysis methods in the tour-
semantically significant objects repre- trajectories? ism, sea monitoring and public transpor-5
The MASTER project
tation domains. plementary domains: tourism, sea mon- one is European non academic and four
Is the privacy preserved? itoring and public transportation. On the are international academic.
The project develops methods based on other hand, the methods that are being The European academic partners are:
privacy-by-design. developed can stimulate new require-
How can we deal with the Big Data ments in the application domains. Big National Research Council of Italy (CNR)
characteristics? Data principles have to be considered participates with the ISTI institute (Isti-
The storage and analysis methods will as part of the methods. Privacy is a per- tuto di Scienze e Tecnologie dell’Infor-
pose emphasis on efficiency and large vasive ethical aspect when dealing with mazione) located in Pisa in Italy and it
scale data management. positioning data, therefore, in MASTER, is the coordinator of the project. The
we have specific tasks for privacy pre- main expertize of CNR researchers are
The consortium at the kick-off meeting
MASTER serving methods for holistic trajectories. in mobility data and semantics, machine
MASTER is a H2020 Marie Sklodows- Furthermore, the consortium is support- learning, data mining for spatio-tempo-
ka-Curie Actions RISE (Research and ed by an Independent Ethical Advisor ral data. The principal investigator and
Innovation Staff Exchange) project. The (Prof. Bettina Berendt) and an Ethical coordinator of the project is Dr. Chi-
overarching objective of MASTER is to Committee (Dr.ssa Rosaria de Luca, Prof. ara Renso. Members of the research
form an international and inter-sectoral Tommaso Piazza, Prof. Celia Zolynski). group are Raffaele Perego, Cristina Io-
network of partners working on a joint A precious first contribution from Prof. ana Muntean, Beatrice Rapisarda, Ida
research programme to answer the Berendt giving her ethical view on two Mele, Vinicius Monteiro de Lira, Andrea
above research challenges. The concept typical cases of privacy in trajectory data Michienzi.
of MASTER is depicted in the figure. We is reported later in the newsletter.
see that the research objective of the University of Ca’ Foscari Venice (UNIVE)
project is to develop methods to build, THE CONSORTIUM is located in Venice in Italy. The main ex-
manage and analyse holistic trajectories. MASTER consortium is formed by ten pertise is in Trajectory Data warehous-
These methods are driven by application synergic and complementary partners: ing, efficient and scalable methods for
scenarios from three different and com- five partners are European academic, storage, mining and quantitative mod-6
MASTER NEWSLETTER - www.master-project-h2020.eu
The MASTER project
elling of agents’ behaviours. Principal is the Thira Municipality (Thira) in the ed in the city of Halifax in the Nova Sco-
Investigator is Dr. Alessandra Raffaeta’ Santorini island in Greece. Thira is repre- tia province in the eastern Canada. DAL
and members of the research group in- sented in MASTER by Christallia Papao- expertize is in machine learning, trajec-
clude Marta Simeoni, Elisabetta Russo, ikonomou who is supporting seconded tory classification, privacy, big data. Prin-
Salvatore Orlando, Claudio Lucchese, Fa- researchers to better understand the cipal investigator is Prof. Stan Matwin.
bio Pranovi, Andrea Marin and Claudio tourism issues of the island, the data Members of the group include Amilcar
Silvestri. that can be collected and the kinds of Soares Junior and Mohammad Etemad.
analysis that can be done on such data.
University of Pireaus Research Center KICK-OFF MEETING
(UPRC) is located in Piraeus in Greece. The international partners are: The Kick off meeting has been a great
Main expertize is in spatio-temporal da- opportunity to meet “live” the European
tabases and analysis methods, privacy, The Federal University of Santa Catari- Academic partners, our Project Officer
big data analysis for movement data. na (UFSC) is located in Florianopolis in Simona Losmanova from REA and the In-
Principal investigator is Prof. Nikos Pele- the state of Santa Catarina in the south dependent Ethical Advisor Prof. Bettina
kis. The research group includes Prof. of Brazil. UFSC experize is on semantic Berendt from University of Leuven.
Yannis Theodoridis. trajectory modelling and similarity mea- The meeting was held in Brussels thanks
sures. Principal investigator is Prof. Vania to the kind hospitality of the CNR Brus-
University of Versailles Saint Quentin Bogorny. Members of the group are Prof. sels office at Rue du Trone, 98 on March
(UVSQ) is located in the west of Paris, Ronaldo Melo, Prof. Luis Otavio Alvares 22, 2018. A total of 13 people partici-
and its science campus in Versailles city. and student Lucas May Petry. pated in the meeting from CNR, UNIVE,
UVSQ main expertize is trajectory data UPRC, UVSQ and HUA. Partner Organiza-
modeling, indexing, mining, as well as The Federal University of Ceara’ (UFC) is tions from Brazil (UFC, UFSC, PUC) and
privacy, with a focus on trajectories fol- located in Fortaleza in the state of Ceara’ Canada (DAL) could participate via re-
lowing a predefined network. UVSQ also in the north of Brazil. UFC expertize is mote connection.
investigates time dependent graphs ei- on mobility patterns and prediction, We had productive discussions and two
ther by aggregation of trajectories or as trajectory reconstruction and graph interactive Question Answering sessions
their underlying context. Principal inves- modelling. Principal investigator is Prof. with the Project Officer and the Inde-
tigator is Prof. Karine Zeitouni. The re- Jose Fernandes de Macedo. Members of pendent Ethical Advisor.
search group includes Prof. Yehia Taher, the group include Francesco Lettich, Igo Indeed, particularly useful has been the
and Prof. Iulian Sandu Popa, Alexandros Brilhante and the students Livia Almada, clarifications of Simona to our questions
Kontarinis and Jingwei Zuo. Ticiana Linhares. on how to implement secondments and
the Prof. Berendt’s vision about ethical
Harokopio University (HUA) is located The Pontifical Catholic University of Rio issues that might arise when dealing
in Athens in Greece. The main expertize de Janiero (PUC) is located in the city of with mobility data.
is in sea monitoring analysis from ves- Rio de Janeiro in Brazil. PUC expertize
sels data, machine learning and big data is in semantic web, social media analysis
analysis. Principal investigator is Prof. and in transportation applications. Prin-
Konstantinos Tserpes. Members of the cipal investigator is Prof. Marco Antonio
group include Iraklis Varlamis. Casanova.
The European non academic partner The Dalhousie University (DAL) is locat-
www.master-project-h2020.eu
Facebook: Master Project H2020
Twitter: Master Project H20207
Holistic trajectories,
privacy, and the strategic concealment/
disclosure of information
A reflection on ethical questions in the mapping of taxi rides and Mediterranean migrant rescue
operations, and the implications of these questions for data-science modelling
Bettina Berendt, Independent Ethics Advisor of MASTER, Department of Computer Science, KU Leuven, Belgium
As the Independent Ethics Advisor (IEA) ethical considerations, it presents more analysis methods for holistic trajectories
of MASTER, I am tasked with “provid[ing] questions than results – the open-end- that are compliant to the privacy-by-de-
support to the consortium in reflecting edness of this text is therefore a feature sign principle.”
on the broader ethical considerations re- and an invitation for carrying the discus-
lated to holistic trajectories”. The Grant sion further. Anonymization and other methods for
Agreement (from which this task is tak- privacy-aware data sharing are certain-
en) further describes that this role com- Specifically, I will share some obser- ly key for the goal of privacy by design,
plements that of the Ethics Committee, vations on data science for improving and MASTER will certainly contribute to
whose task is to “guarantee the good humanitarian rescue operations in the the emerging field of data privacy for
governance of data and the research in- Mediterranean, a timely topic area with rich spatiotemporal data. Linked to this
tegrity and academic ethics” as well as lots of spatiotemporal data and even and equally undisputed is the necessity
to ensure “compliance with ethical and more options for creating, analysing and to observe data protection law and be
legal framework in case additional da- predicting holistic trajectories. one of the first projects to demonstrate
tasets will become available during the how to effectively do data science under
lifetime of the project”. To fill the chal- BACKGROUND: HOLISTIC TRA- the European Union’s General Data Pro-
lenging role of IEA, I have worked out, JECTORIES, PRIVACY, DATA SCI- tection Regulation (GDPR), which came
together with the consortium, several ENCE, AND THE MASTER AP- into effect two months after the start of
concrete steps, in particular documen- PROACH MASTER. (MASTER faces the additional
tation and interaction provisions, which Many holistic trajectories involve data interesting challenge that some of the
are described in an internal Deliverable. and inferences on human mobility, and consortium members operate under
Our plan is to describe experiences in human mobility is well-known as a field other jurisdictions, but this is not the
and insights from this process in publi- that raises many legal and ethical issues. topic of the present text.)
cations, with the aim of sharing lessons The MASTER Grant Agreement summa-
learned with future projects. Before the rizes the challenges and the approach But are data privacy and GDPR compli-
(necessarily ex post) publication(s), this of the project: “The location of a mobile ance all there is to an ethically reflected
line of activities is likely to be approach to holistic trajectory
of interest primarily to project analysis? What other questions
members themselves. MASTER will certainly contribute to the surface when one considers dif-
emerging field of data privacy for rich spatio- ferent use cases?
So what could be contributions temporal data
of the IEA during the project that I will investigate two examples of
are interesting to a wider public vehicle trajectory data. The first
and therefore fit a newsletter? I believe user represents very sensitive informa- is the New York taxi rides dataset. The
this should be reports from inspiring dis- tion and it has been shown … that the reception of this dataset represents a
cussions in and around MASTER’s topics simple obfuscation of the location data standard example of today’s discussions
that illustrate selected ethical questions or the user identifier do not grant priva- in data science around privacy-sensitive
around data science and the activities of cy: an attacker could correlate the coarse mobility datasets, and it was, at least
data scientists, and that highlight why location provided with background for me, the initial “blueprint” for iden-
and how the task of reflecting on broad- knowledge to try to identify the location tifying key questions to be asked of a
er ethical considerations differs from with higher precision. … [With] contex- research project dealing with vehicle
those around data governance, research tually enriched trajectories, the privacy trajectory data. The second is an anal-
integrity, academic ethics, and compli- problem may become even more chal- ysis of AIS ship location data to study
ance. The present text is the first in this lenging. … [W]e plan to cope with this rescue operations at sea, and a brief
planned series. As often happens with challenge by studying management and description of the wider data ecosystem8
MASTER NEWSLETTER - www.master-project-h2020.eu
Holistic trajectories, privacy, and the strategic concealment/disclosure of information
related to migrant movements in the the sense that at least some, and likely ate a type of holistic trajectories, manu-
Mediterranean. This example illustrates many, taxi drivers and taxi customers are ally label them as representing (or not) a
that even “privacy” takes on a different easily identifiable, the dataset contains rescue operation, and use clustering and
meaning in this context, that legal and personal data. Taxi customers (and con- machine learning with a view to classi-
technological questions relevant in the ceivably also taxi drivers) had not been fication and prediction (The enriching
first example do not appear applicable, asked to give their consent to these data data in this case include broadcast warn-
and that instead the example points to being published online for unspecified ing data produced by WWNWS, a global
many further questions that researchers purposes, nor are other grounds for service managed by the UN Maritime
should ask. While migrant phenomena such processing (Article 6 GDPR) pres- Organization IMO, and the tweets issued
and sea rescue operations are no doubt ent. This is textbook privacy violation by NGO vessels).
a particularly politically charged environ- by data (more accurately in the EU con-
ment, I believe that many of these ques- text: a violation of data protection law), Other researchers, including from the
tions are relevant for other contexts of and therefore, data protection / ethics MASTER project, have investigated how
applied research too. boards in EU universities strongly dis- to model and detect such trajectories.
courage the use of this dataset for any Based on AIS data, complex events, in-
CASE STUDY 1: NEW YORK CITY kind of data mining. (This is anecdotal cluding but not limited to SAR (search
TAX RIDES DATASET evidence, gathered not at the universi- and rescue) missions, and involving one
In 2014, the City of New York released, ties of the MASTER partners.) or several vessels, can be modelled and
in response to a Freedom of Information detected efficiently and in real time us-
request, data about all 173 million taxi This perception of a dataset assumes ing combinations of exploratory, ma-
rides in New York in 2013, with the taxi that the population of data subjects con- chine learning, and logics-based (event
identifiers pseudonymised, and exact sists of informed individuals, who exer- calculus) techniques (Patroumpas et al.,
spatiotemporal data about start- and cise their autonomy among other things 2017; Varlamis, Tserpes, & Sardianos,
endpoints, as well as fares, given. This by travelling in vehicle passages they pay 2018).
dataset provided a rich real-life dataset for, and who have a reasonable expecta-
for a wide range of data mining studies, tion of privacy in doing so that requires Hoffmann et al. mention several limita-
such as “optimization of the revenue that the data about their movements re- tions of their method, mainly with re-
of NYC Taxi Service using Markov Deci- main confidential. The main question for gard to data quality, including the fact
sion Processes” (Li, Bhulai, & van Essen, the responsible data scientist appears to that as circumstances change, so do the
2017). At the same time, the publication follow from the observation that the re- data and patterns (thus, the analysis of
of the dataset was soon criticized on moval of taxi identifiers “would adverse- timely data is crucial).
privacy grounds. For example, the taxi ly impact certain types of analysis on the
pseudonyms could easily be re-identi- data” (Douriez et al., 2016, p. 148) and Under the heading of “privacy”, they
fied to their actual medallion numbers the need to find different analysis types. raise several points. The first is a refer-
(Pandurangan, 2014). It was also ar- ence to concerns over port security as a
gued that the data allowed inferences CASE STUDY 2: AIS DATA FOR consequence of AIS data being publicly
towards sensitive attributes of the taxi DESCRIBING MIGRANT RESCUE available. The second is the possibility
drivers, such as the patterns of breaks OPERATIONS that rescue organisations may not want
during the day indicating that someone The second case study is based on a the full details of their operations to be
is a devout Muslim (uluman, 2015). Fi- paper published in a report by the IOM publicly known, because they are facing
nally, with some background knowledge, (Hoffmann et al., 2017), the UN Interna- opposition and threats (a European far-
inferences can be made towards the tional Organization for Migration, and right group threatening to attack rescue
identity of taxi customers, and based on illustrated in an interactive and multi- vessels is mentioned). Both concerns
that, details about their whereabouts media online presentation (see: http:// are not privacy concerns in the sense of
learned (Atockar, 2014). The futility even rescuesignatures.unglobalpulse.net/ European law (in particular because the
of better pseudonymisation/anonymi- mediterranean/). As in case study 1, the agent requesting the confidentiality is
sation approaches was demonstrated base data are in principle publicly acces- not a natural person). As a third reason,
by Douriez et al. (2016). Medallion and sible. They are data from the Automatic the authors mention that “adversarial
driver license IDs were removed from Information System (AIS), a maritime users could take advantage of the data
NYC’s taxi datasets released in subse- communications system through which to track the location of individual refu-
quent years. vessels regularly broadcast information, gees [identified by record linkage with
(https://data.cityofnewyork.us/ including their identifier, vessel type, lat- data such as photos or statements, or
browse?q=taxi) itude and longitude, speed, course and other background knowledge], attack
destination. The information is used by rescue boats or guide piracy operations”
The taxi rides represent a typical case of maritime authorities and ships to lo- (p. 40). Presumably, the attacks and pi-
personal data in the sense of the GDPR. cate nearby vessels and avoid collisions. racy operations are security/safety con-
Personal data are “any information relat- Based on these spatiotemporal data and cerns of the rescue vessels, and these
ing to an identified or identifiable natu- enriched with textual and pictorial data concerns could arise from the public
ral person (‘data subject’)” (Article 4). In from other sources, the authors gener- availability of the data as well as from9
Holistic trajectories, privacy, and the strategic concealment/disclosure of information
possible predictors learned from them, Berendt, 2010). because traditional approaches to (for
i.e. the data scientists’ work. example) anonymisation are focussed
A second question related to privacy is on the protection of individuals from
It also appears, from the sentence, that related to the referent of the data. Tech- threats against persons as individuals. It
the possible tracking of individuals is con- nically a ships’ trajectory could be con- is an open research question what could
sidered a security/safety risk (because it sidered personal data in the same sense constitute effective measures of group
could lead to attacks) rather than a typ- as a taxi’s trajectory. (This concerns protection.
ical privacy risk (by which an individual the ships provided by the traffickers as
migrant would want to keep their iden- well as rescuing ships once they have Data privacy, viewed technically, does not
tity or properties hidden). It is difficult been boarded by migrants.) However, need to make a clear distinction between
to say what role such expectations of, the chances appear slim that individu- protecting information and control over
or wishes for, privacy in our usual sense, als would be identified like in the ded- it related to individuals (a concept root-
play in this extreme situation. Also, icated attacks in the taxi example, and ed in human rights) and protecting in-
it has been formation and
observed in- control over
creasingly it related to
over the past other entities
years that (such as or-
rather than ganisations,
trying to hide the NGOs in
their voyage, the current
“migrants example and
from Libya fa- in the argu-
cilitated their ment made
traceability by Hoffmann
by national et al., a con-
authorities cept rooted in
and monitor- IT security). In
ing systems, data privacy, a
a nt i c i p at i n g different and
in space and independent
time border dimension
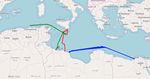
patrols by The Alexander Maersk trajectory rescuing refugees in the Mediterranean Sea becomes rel-
sending an evant when
SOS as soon as they entered the inter- it is unclear whether they would even one asks “whose privacy” should be
national waters” (Tazzioli, 2016, p. 576). be identifiable. In this sense, then, AIS- protected. A useful distinction is that
In other words, along their journey, mi- based trajectories of rescuing ships may between data owner, data respondent
grants deal strategically with visibility not count as personal data. In fact, as (the data subject, although not always in
and invisibility, with information disclo- has been argued in this context (Tazzioli, its legal sense of an individual person),
sure and hiding/confidentiality. This is 2016) as well as in connection with other and data user; and this distinction has
quite probably a very rational strategy applications of big data analyses to hu- implications for the choice of data-priva-
given the fact that a successful and invis- manitarian causes (Taylor, 2017), there cy protection methods (Domingo-Ferrer,
ible journey to Europe is by now nearly is a temptation to focus on migrants as a 2007). In the present example, one as-
impossible for many reasons, including group defined only by one feature (here: signment of these roles that follows the
that traffickers severely overload and to be in need of rescue). argument about risks above could be:
under-equip their vessels, and that due the NGO as the data owner, the migrant
to the high-resolution sensors employed The fact that big data constitute new (or migrant group) as the data respond-
in the European Border Surveillance Sys- risks in the profiling of groups has been ent, and various (potential) data users:
tem EUROSUR (Deibler, 2015), even very lamented often in connection with data the public, politicians, pirates, ...
small vessels are likely to be spotted and protection laws such as the GDPR (which
monitored. Strategic information disclo- focus on the protection of individuals’ Moving beyond privacy and data priva-
sure (in addition to strategic information rights and freedoms); in the humanitar- cy, many other questions, technical as
hiding) by individuals can also be ob- ian realm, it creates additional and dif- well as ethical, arise about information
served in many other contexts that are ferent challenges (Taylor, van der Sloot, disclosure and hiding. The study and
less dramatic than the life-or-death situ- & Floridi, 2017). visualisation of “rescue patterns” can
ations faced by migrants on the Mediter- have different objectives. Hoffmann et
ranean, and it has been pointed out that For the data scientist, this means that al. mention operational objectives (e.g.,
strategic information disclosures too can also the response to these risks and supporting coordination of rescue oper-
be privacy-related behaviour (Gürses & threats may need to be very different, ations), analytic objectives (e.g., deter-10
MASTER NEWSLETTER - www.master-project-h2020.eu
Holistic trajectories, privacy, and the strategic concealment/disclosure of information
mining conditions under which rescues In the following paragraphs, I will illus- (Ziniti, 2018). Can these aspects be mod-
are most effective), and reporting ob- trate three examples of these consider- elled as part of multi-aspect trajectories,
jectives. The latter are described as fol- ations. and how could this be done if the datum
lows: “supplement the large amount of itself is still being contested?
qualitative, descriptive coverage already First, sometimes trajectory data illus-
produced by NGOs and the news me- trate very directly the influences of
In sum, an ethical consideration of the
dia”, “help external observers … obtain context and the uncertainty and the modelling and reporting of vehicle data
a high-level picture of what is happening “unknowns” of vessel operators. As an
and patterns, even if restricted to what
in the region over time. An overview of example, consider the recent case of a
data are to be included and how, what
these patterns is critical for coordina- commercial cargo ship that took on 113
information is to be kept confidential or
tion and advocacy purposes; it enables people saved by an NGO rescue ship and
disclosed, can reach far beyond the tra-
stakeholders to see the true magnitude then spent four days in a political stand-
ditional questions discussed under data
of rescue operations, and to quantify off on a zig-zag trajectory between ports
protection and data privacy. It requires
costs, shortcomings and future needs.” before being allowed to dock in Sicily (Al
a critical examination of the sociopolit-
(Hoffmann et al., 2017, p. 30) ical background of the mobil-
Although data can help citizens demand accounta- ity that these vehicles afford,
Concentrating on the report- support, or impede, and of
ing objective, it can be argued bility, ultimately, the inferences that can be drawn the goals of the data-science
that rescue patterns constitute from the data are only as valuable as the actions project undertaken. And al-
a counter-mapping practice: in they induce. though “data can help citizens
the EUROSUR monitoring sys- demand accountability”, “ul-
tem, selected migratory events timately, the inferences that
are produced from the sensed data and Jazeera, 2018; Borghese et al., 2018) (I can be drawn from the data are only
mapped in time and space (Tazzioli, thank Konstantinos Tserpes for mention- as valuable as the actions they induce.
2016). The website watchthemed.net, ing this example and making available … this problem will not be solved with
initiated and run by a network of NGOs, the visualization of the trajectory). Can data alone” (Hoffmann et al., 2017, p.
activists and researchers, maps events and should holistic trajectories measure 42). This added complexity may be what
to monitor deaths and violations of mi- and visualize the enormous costs caused makes data science projects “for social
grants’ rights. In the SAR-centric appli- by such decisions, as well as the incen- good” so fascinating and worthwhile. I
cations described here, rescue events tives and influences this may have on look forward to feedback on this essay
are produced and mapped. EUROSUR is further behaviour by vessel operators? and to future work in the area!
run by Frontex, and its data and analyt- Second, many of the existing, but not
ics are not available to NGOs and other accessible data have strong effects on
external partners, whereas the rescue the rescue events modelled. For exam-
patterns are mined from data available ple, the Libyan coastguard now has indi- REFERENCES
publicly (AIS data) or to partners of the rect access to EUROSUR data (Monroy, Al Jazeera News (2018). Danish car-
go ship carrying refugees allowed to dock
research (the broadcast warnings), and 2018); thus, their rescue actions, includ- in Italy. 26 June 2018. https://www.alja-
enriched with further aspects from pub- ing those in cooperation or competition ze e ra . co m /n e w s / 2 0 1 8 / 0 6 /d a n i s h - c a r-
lic data (such as tweets). with European actors, may be planned go-ship-carrying-refugees-allowed-dock-ita-
based on data that are not modelled in ly-180626081632471.html
Mapping practices generate a narrative the rescue patterns system, and which Atockar (2014). Riding with the Stars: Passen-
around their real-world phenomenon. therefore can co-determine the “coordi- ger Privacy in the NYC Taxicab Dataset. https://
The current data models and visualiza- nation” and “effectiveness” of a rescue. research.neustar.biz/2014/09/15/riding-with-
tions of rescue patterns, maybe for tech- Can and should these data (or at least the-stars-passenger-privacy-in-the-nyc-taxi-
cab-dataset/
nical reasons (because the EUROSUR the fact of their existence and possible
data are not available), maybe to avoid influence) be modelled? Borghese, L., Vandoorne, S., & Vonberg, J.
visual clutter, display these patterns in (2018). Migrant rescue ship Lifeline to dock
an otherwise “empty” space. Is it possi- Third, further questions concern which in Malta after being stranded for five days in
the Mediterranean. CNN News, 26 June 2018.
ble, and is it advisable, to at least repre- aspects are important to judge the legal https://edition.cnn.com/2018/06/26/europe/
sent that far more data exist (even if one and ethical dimensions of a rescue op- migrant-ships-maersk-lifeline-intl/index.html
does not have access to them)? In other eration (cf. Medina, 2018, resp. Cancel-
words, should the “known unknown” lato, 2018): in a recent case in which a Cancellato, F. (2018). Poche palle, i migranti
della Asso 28 li abbiamo respinti noi: e la Lib-
data be modelled and represented too, commercial towboat under Italian flag ia è solo la foglia di fico della nostra ipocrisia.
and if so, how? These data are impor- rescued migrants and then handed them Linkiesta, 1 August 2018.
tant for technical reasons as much as for over to the Libyan coastguard, a key le- h t t p s : // w w w . l i n k i e s t a . i t / i t / a r t i -
narrative reasons – how can and should gal question revolves not around the cle/2018/08/01/poche-palle-i-migranti-del-
la-asso-28-li-abbiamo-respinti-noi-e-la-li-
these two motivations be addressed, spatiotemporal data of the rescue oper- bi/39019/
and how can the choices made be made ation, but on whether it was instructed
in a transparent and accountable way? by the Italian or the Libyan authorities Deibler, D. (2015). EUROSUR – A Sci-fi Border
Zone Patrolled by Drones? In J. Camenisch, S.11
Holistic trajectories, privacy, and the strategic concealment/disclosure of information
Fischer-Hübner, & M. Hansen (Eds.), Privacy ume_3_part_1.pdf oping World. In L. Taylor, B. van der Sloot, &
and Identity Management for the Future In- L. Floridi (Eds.), Group Privacy: the Challenges
ternet in the Age of Globalisation (pp. 87-109). Li, J.P.K., Bhulai, S., & van Essen, T. (2017). of New Data Technologies. Berlin etc.: Spring-
Berlin etc.: Springer. Retrieved from https://hal. Optimization of the revenue of the New York er. Available at SSRN: https://ssrn.com/ab-
inria.fr/hal-01431600/document City Taxi Service using Markov Decision Pro- stract=2848825
cesses. In Proc. of DATA ANALYTICS 2017:
Domingo-Ferrer, J. (2007). A three-dimension- The Sixth International Conference on Data Taylor, L., van der Sloot, B., & Floridi, L.
al conceptual framework for database privacy. Analytics. Retrieved from https://www.think- (Eds.) (2017). Group Privacy: the Challeng-
In Proc. SDM 2007 (pp. 193–202). Berlin etc.: mind.org/download.php?articleid=data_analyt- es of New Data Technologies. Berlin etc.:
Springer, LNCS 4721. Retrieved from https:// ics_2017_4_10_68005 Springer. https://www.springer.com/de/
crises-deim.urv.cat/webCrises/publications/ book/9783319466064
lncs/lncs4721.pdf Medina, J. (2018). U.N. says migrants’ return to
Libya by Italian boat could be illegal. Reuters, Tazzioli, M. (2016).Eurosur, humanitarian
Douriez, M., Doraiswamy, H., Freire, J., & Silva, 31 July 2018. https://www.reuters.com/arti- visibility, and (nearly) real-time mapping in
C.T. (2016). Anonymizing NYC Taxi Data: Does cle/us-europe-migrants-libya/migrants-return- the Mediterranean. Acme, 15 (3), 561-579.
It Matter? In Proc. 2016 IEEE International to-libya-by-italian-boat-could-breach-interna- https://acme-journal.org/index.php/acme/ar-
Conference on Data Science and Advanced An- tional-law-u-n-idUSKBN1KL1K4 ticle/view/1223/1201
alytics (DSAA), Montreal, QC, 2016 (pp. 140-
148). Retrieved from https://vgc.poly.edu/~ju- Monroy, M. (2018). Durch die Hintertür: uluman (2015). Identifying Muslim cabbies
liana/pub/taxi-privacy.pdf Anschluss Libyens an europäische Überwa- from trip data and prayer times. https://
chungssysteme. CILIP Blog, 19 January 2018. www.reddit.com/r/dataisbeautiful/com-
Gürses, S.F. & Berendt, B. (2010). The Social h t t p s : // w w w . c i l i p . d e / 2 0 1 8 / 0 1 / 1 9 / ments/2t201h/identifying_muslim_cabbies_
Web and Privacy. In E. Ferrari & F. Bonchi durch-die-hintertuer-anschluss-libyens-an-eu- from_trip_data_and/
(Eds.), Privacy-Aware Knowledge Discovery: ropaeische-ueberwachungssysteme/
Novel Applications and New Techniques. Boca Varlamis, I., Tserpes, K., & Sardianos, C. (2018).
Raton, FL: Chapman & Hall/CRC Press, Data Pandurangan, V. (2014). On Taxis and Rainbows “Detecting Search and Rescue Missions from
Mining and Knowledge Discovery Series. Re- Lessons from NYC’s improperly anonymized AIS Data,” 2018 IEEE 34th International
trieved from taxi logs. https://tech.vijayp.ca/of-taxis-and- Conference on Data Engineering Workshops
https://www.esat.kuleuven.be/cosic/publica- rainbows-f6bc289679a1 (ICDEW), Paris, 2018 (pp. 60-65). http://iee-
tions/article-1304.pdf explore.ieee.org/stamp/stamp.jsp?tp=&ar-
Patroumpas, K., Alevizos, E., Artikis, A., Vodas, number=8402020&isnumber=8402003
Hoffmann, K., Boy, J., Leon-Dufour, J., Breen, M., Pelekis, N., & Theodoridis, Y. (2017). Online
D. Earney, C. & Luengo-Oroz, M. (2017). Using event recognition from moving vessel trajecto- Ziniti, A. (2018). Migranti, inchiesta sul com-
big data to study rescue patterns in the Med- ries. GeoInformatica, 21(2), 389-427. https:// portamento del rimorchiatore italiano Asso
iterranean. In: Fatal Journeys. Volume 3, Part link.springer.com/article/10.1007/s10707- 28. La Repubblica, 8 August 2018. http://
1: Improving Data on Missing Migrants (pp. 016-0266-x www.repubblica.it/cronaca/2018/08/08/
24-46). Geneva, Switzerland: International Or- news/migranti_presentato_un_esposto_sul_
ganization for Migration. https://publications. comportamento_del_rimorchiatore_italiano_
Taylor, L. (2017). Safety in Numbers? Group
iom.int/system/files/pdf/fatal_journeys_vol- asso_28-203654671/
Privacy and Big Data Analytics in the Devel-This project has received funding from the European Union’s Horizon 2020 research and
innovation programme under the Marie Sklodowska-Curie grant No 777695
Duration: March 1 2018 | February 28 2022
Editorial Secretariat
master-info@isti.cnr.it
Editorial Board
Chiara Renso
Beatrice Rapisarda
Cristina Muntean
Layout and Design
Beatrice Rapisarda
Copyright notice
All authors, as identified in each article, retain copyright of their work.
The authors are responsible for the technical and scientific contents of their work.
Privacy statement
The personal data (names, email addresses…) and the other information entered in MASTER Newsletter will be treated according with
the provision set out in Legislative Degree 196/2003 (known as Privacy Code) and subsequently integration and amendment.
Coordinator of the project: Chiara Renso | chiara.renso@isti.cnr.it
MASTER Newsletter is not for sale but it is distributed for purposes of study and research and published online at
http://www.master-project-h2020.eu
Consiglio Nazionale
delle Ricerche
ip
unic ality
M
of
T h iraYou can also read